
How to Evaluate Endpoint Protection Solutions [Checklist]
How do you evaluate which endpoint protection solution is best for your needs? Choosing the right cybersecurity solution for your organization can be a challenging process. Not only do you have to consider your organization’s size, but you also need to make sure that every single endpoint is protected against cyberattacks.
Asking the right questions can point you to the right endpoint protection solution. Below, we’ll outline how you can evaluate cybersecurity solutions to find the best tool for your business.

What is endpoint protection?
Endpoint protection is a cybersecurity solution that prevents endpoints from being exploited. Endpoints are any device connected to your network that can be susceptible to attacks.
Examples include:
Computers
Laptops
Mobile phones
Servers
IoT devices
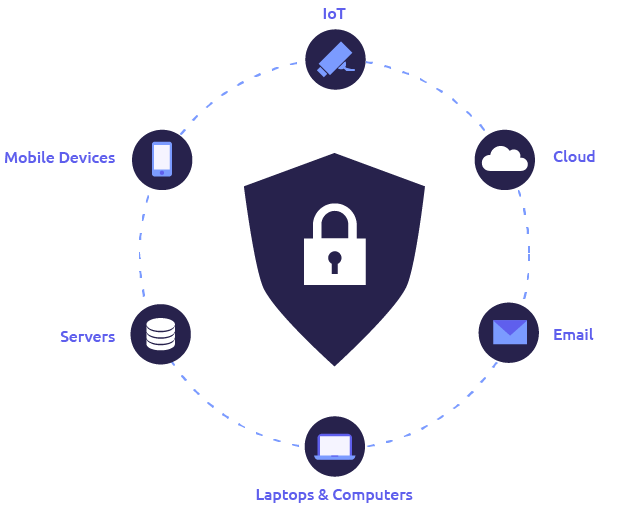
The key benefit of utilizing a cloud-based endpoint protection solution is that the protected devices will share information about threats with each other automatically — helping prevent similar vulnerabilities from compromising a different device within your network. This is because tools in an endpoint protection platform are combined, not separate; all of these tools work together to make sure your network is secure.
Generally, there are 2 different types of endpoint protection solutions: endpoint protection platform (EPP) and endpoint detection and response (EDR).
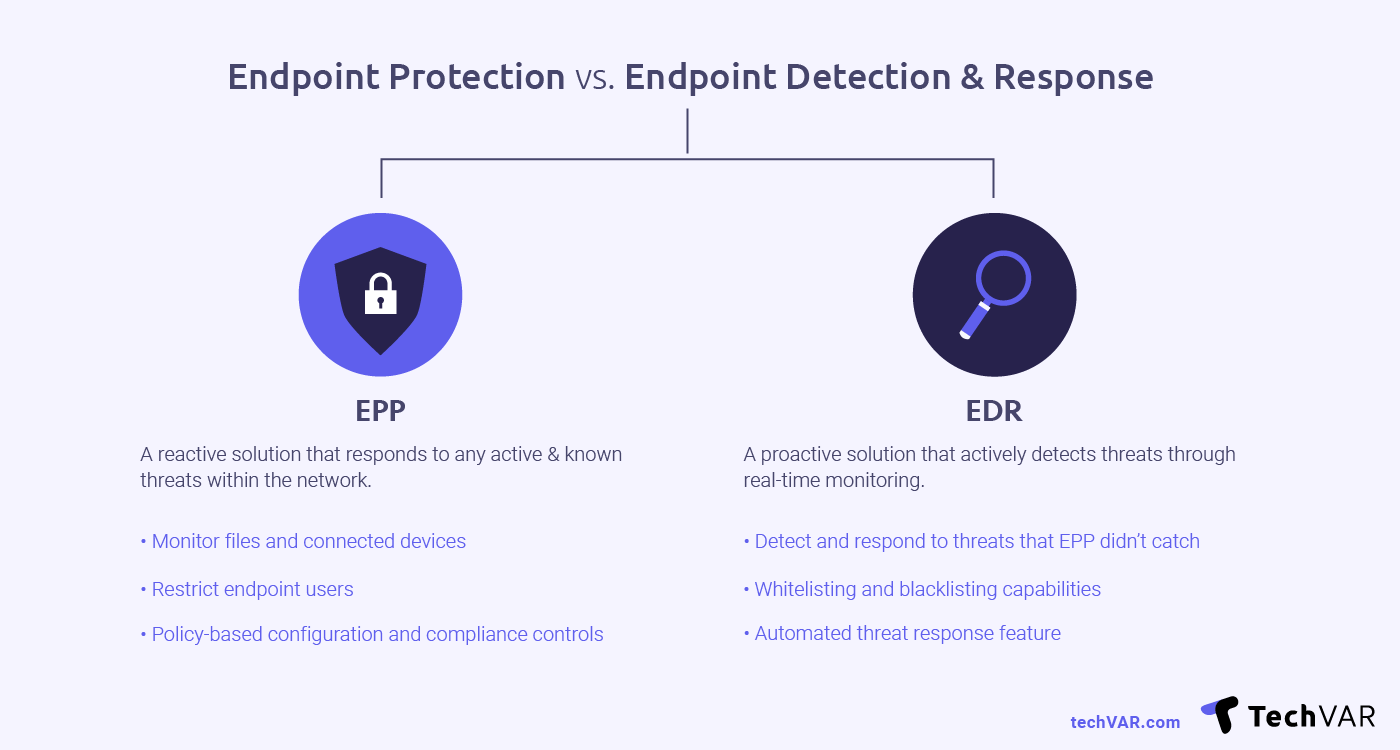
EPP vs. EDR
An endpoint protection platform is a reactive solution that responds to any active and known threats within the network. You can monitor files and connected devices on a scheduled basis or do so continuously. It can also restrict endpoint users from accessing websites and applications. There are policy-based configuration and compliance controls you can take advantage of to make sure your system stays protected.
Endpoint detection and response is a proactive solution that actively detects threats through real-time monitoring. EDR solutions can detect and respond to threats that your EPP did not catch. IT managers utilize the whitelisting and blacklisting capabilities to actively prevent vulnerabilities and boost productivity. There are also automated threat response features — making it easier to respond to threats more efficiently.
A common misconception is that smaller organizations do not need to invest in an EDR because hackers won’t target smaller businesses. In reality, cybercriminals assume that SMBs have small budgets and less robust cybersecurity, which makes smaller businesses easier targets for cyberattacks.
That’s why many organizations have a mix of both EPP and EDR in their suite. Nowadays, there are many next-generation endpoint protection solutions that also include EDR’s key features; this makes it easier for you to protect all of your users at an affordable cost.
Before you start evaluating endpoint protection vendors
You’ll first need to start evaluating your current cybersecurity solution — if you have one already. Understand your current solution’s capabilities and how it matches up against your requirements. What is it lacking that you wish it had?
Consider the following questions:
Can your current solution cope with the most sophisticated attacks?
Is it giving you enough management flexibility?
Does it support remote work?
Does it have data protection with encryption management?
Does your EPP include EDR?
Then, it’s time to look at your business holistically and take notes on key factors that will determine which new solutions stand out to you.
Number of Endpoints & Users
When looking for a solution that better suits your needs, you need to consider the number of users and the number of endpoints you need to protect. Make sure your new solution can protect everyone in the company — even the new employees who are about to be onboarded.
Budget
Next, think about your budget. While it’s important to keep in mind that the most expensive EPP/EDR doesn’t necessarily equate to effectiveness, keeping your budget realistic helps weed out solutions that won’t meet your requirements. Some vendors even offer group discounts, making it more affordable for you to protect your entire organization.
Risks
Finally, think about your biggest cybersecurity risks. For example, if your colleagues aren’t as tech-savvy, they might be more vulnerable to phishing attacks. If you’re in the healthcare or government sector, you might be more worried about data loss — as attackers know your organization has sensitive data, such as SSN, addresses, and credit card numbers.
Other risks we commonly see on our clients’ radar are ransomware and IoT attacks. Keep in mind that each business has its own set of unique threats, so be sure to read up on the latest cyberattacks that occur within your industry.
Remember: you’re as strong as your weakest link, so make sure your next solution can protect you against your biggest threats.
How to evaluate endpoint protection solutions
With the abundance of endpoint protection solutions out there, it’s no surprise that there are many features available in the market.
These are a few of the most popular features our customers usually look for:
Email security
File security
Device control
Application control (with whitelisting and blacklisting capabilities)
To make evaluation easier, we recommend listing out at least 3 vendors you’re interested in and their respective point of contact. You can also consult a reseller if you’re still struggling with which solution to pick. For example, TechVAR’s tech advisors evaluate your tech needs by factoring in both your goals and limitations to find the best solution for you.
As you’re narrowing down which endpoint protection solution to use, consider these factors:
- Market feedback: Understand what the market is saying about the vendor and solution. Take advantage of free review and rating sites and read through customer feedback to see if the solution can truly deliver on its promises. Two credible sites to look into are Gartner’s Magic Quadrant and Gartner’s Peer Insights.
- Vendor history: How long has the vendor been in business? Although an older business does not always translate into a higher success rate, it’s safe to say that a seasoned organization tends to have more credibility. Be sure to read into the vendor’s past and understand how they’ve grown over the years.
- Endpoint integration: You don’t want to give hackers an opportunity to compromise your organization. Make sure that the solution can cover all of your current and future endpoints easily, including desktops, laptops, servers, and IoT devices.
- Ease of rollouts: Your chosen solution should make it easy for your IT team to roll out any new cybersecurity initiatives you may have, especially when working remotely. Otherwise, you may waste time choosing a different solution down the line.
- Fit with your requirements: With all of the salespeople’s pitches and product demos, it’s easy to forget why you’re looking into a new solution in the first place. While it’s nice to have extra features, understand whether the proposed solution addresses all of your initial requirements.
- Fit with your budget: Implementing a new endpoint protection solution is ultimately an investment for your organization. Make sure your solution fits within a realistic budget. After all, just because a product is expensive doesn’t mean that it’s the best solution for your organization’s unique needs.
- Quality of support: Evaluate how the vendor will support you when issues arise. Are you able to reach them easily — even during regular off-hours? What about if your regular point of contact is unavailable? Note that if you purchase through a reseller, their partnership with the vendor can often help you get more responsive support.

A final word on finding the best endpoint protection for your business
We’re here to make finding the right endpoint protection solution for your organization easier. Use the 7 factors above to see how potential solutions measure up to your requirements.
Remember: it’s not enough to just rely on technology to prevent cyberattacks. Be sure to invest in employee training so your colleagues can spot the signs of phishing, understand the dangers of using public networks, and know best practices on data loss prevention.
If you’re struggling to find the best tech for your business, reach out to our technology advisors. With over 300 partners, we are able to bring multiple solutions to the table for you to evaluate, keeping your requirements in mind and matching you with the most cost-effective solution.
Let our experts find the perfect cybersecurity solution for your needs.
TechVAR is your personal shopper for all your IT needs.
